Having REFERENCES is WILD : Hacker takes a strangely corporate approach to scamming a woman out of thousands
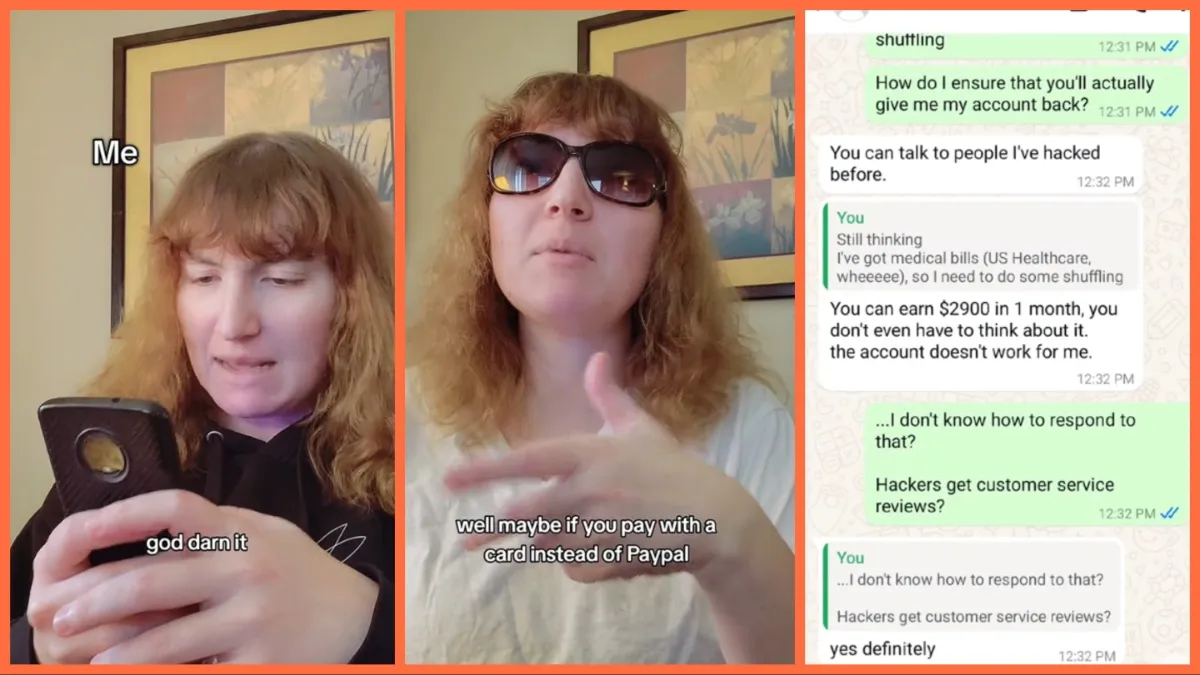 Get the Full StoryGenerally speaking, there is a time and place for everything. Diplomacy and civility, for instance, are welcome and expected when it comes to international affairs involving tariff discussions not pointing any fingers , but it s the last thing one might expect in an exchange with a cyber criminal. Perhaps this is why the plight of TikTok s c.m.alongi_author strikes us as so impossibly hilarious. Of all the the ways that C.M. could have spent their morning, the triple threat of entering the crypto world, negotiating the release of their account like a hostage situation, and collaborating on their own theft was probably the last thing they were expecting. c.m.alongi_author My hacker story. Obviously I got the old account back, but all new CaFae content will be c.m.alongi_cafae #hack #hacker #storytime #silly #humor original sound c.m.alongi_author Over the course of the four-and-a-half minute video from the very account that fell into the hands of this oxymoronically tactful hacker , C.M. recites a lightly-paraphrased version of a real conversation that they had with someone who stole their TikTok account and demanded payment for its release. Luckily, C.M., being an author, has likely seen enough movies to know better than to take the hacker s promise at face value, and suggests a deal where they pay the hacker half the amount they want for the account s release, and then send the other half to make good on the honesty system that frankly has no place in an exchange like this. What follows is a hilariously exhausting back and forth of how exactly the hacker will receive their payment, involving crypto IDs, multiple new apps that C.M. needs to download, and inadvertent cooperation from a few American banks that are ostensibly none the wiser. But by far, best part of this entire conversation is the hacker claiming that the people they ve hacked in the past would be willing to vouch for the hacker s track record of being taken at their word, as if that would render C.M. s aforementioned deal moot. As one commenter pointed out, Having REFERENCES is WILD. Others just generally lost their minds at how uncannily polite the hacker was about C.M. taking the time to hear them out; Thank you for trying and taking the time. from a hacker is CRAZY, referencing the screenshots of the actual conversation that C.M. provides at the end of the video. As far as dealing with hackers go, C.M. s approach here was questionable, but undeniably effective, seeing as she seemingly didn t pay the hacker and wound up getting her account back anyway for which C.M. no doubt became the latest name on the hacker s apparently long list of endorsers . According to iHasco.com, though, the more correct approach would be to change your password, enable update your security questions, and double-check all of your devices to determine where a breach could have come from. Of course, they left out the most effective countermeasure of cybersecurity, which is to cooperate fully with the hacker, but also present yourself as so technologically incompetent that they inevitably lose their temper and blacklist you from their potential targets. Indeed, if this is the career they chose, you might as well make them work for it, or at least incentivize them to use their talents for good.
Get the Full StoryGenerally speaking, there is a time and place for everything. Diplomacy and civility, for instance, are welcome and expected when it comes to international affairs involving tariff discussions not pointing any fingers , but it s the last thing one might expect in an exchange with a cyber criminal. Perhaps this is why the plight of TikTok s c.m.alongi_author strikes us as so impossibly hilarious. Of all the the ways that C.M. could have spent their morning, the triple threat of entering the crypto world, negotiating the release of their account like a hostage situation, and collaborating on their own theft was probably the last thing they were expecting. c.m.alongi_author My hacker story. Obviously I got the old account back, but all new CaFae content will be c.m.alongi_cafae #hack #hacker #storytime #silly #humor original sound c.m.alongi_author Over the course of the four-and-a-half minute video from the very account that fell into the hands of this oxymoronically tactful hacker , C.M. recites a lightly-paraphrased version of a real conversation that they had with someone who stole their TikTok account and demanded payment for its release. Luckily, C.M., being an author, has likely seen enough movies to know better than to take the hacker s promise at face value, and suggests a deal where they pay the hacker half the amount they want for the account s release, and then send the other half to make good on the honesty system that frankly has no place in an exchange like this. What follows is a hilariously exhausting back and forth of how exactly the hacker will receive their payment, involving crypto IDs, multiple new apps that C.M. needs to download, and inadvertent cooperation from a few American banks that are ostensibly none the wiser. But by far, best part of this entire conversation is the hacker claiming that the people they ve hacked in the past would be willing to vouch for the hacker s track record of being taken at their word, as if that would render C.M. s aforementioned deal moot. As one commenter pointed out, Having REFERENCES is WILD. Others just generally lost their minds at how uncannily polite the hacker was about C.M. taking the time to hear them out; Thank you for trying and taking the time. from a hacker is CRAZY, referencing the screenshots of the actual conversation that C.M. provides at the end of the video. As far as dealing with hackers go, C.M. s approach here was questionable, but undeniably effective, seeing as she seemingly didn t pay the hacker and wound up getting her account back anyway for which C.M. no doubt became the latest name on the hacker s apparently long list of endorsers . According to iHasco.com, though, the more correct approach would be to change your password, enable update your security questions, and double-check all of your devices to determine where a breach could have come from. Of course, they left out the most effective countermeasure of cybersecurity, which is to cooperate fully with the hacker, but also present yourself as so technologically incompetent that they inevitably lose their temper and blacklist you from their potential targets. Indeed, if this is the career they chose, you might as well make them work for it, or at least incentivize them to use their talents for good.Share: